Blog Archive
Blog Archive 2017
 ,
,  ,
,  ,
,  ,
,  ,
,  ,
,  ,
,  ,
,  ,
, 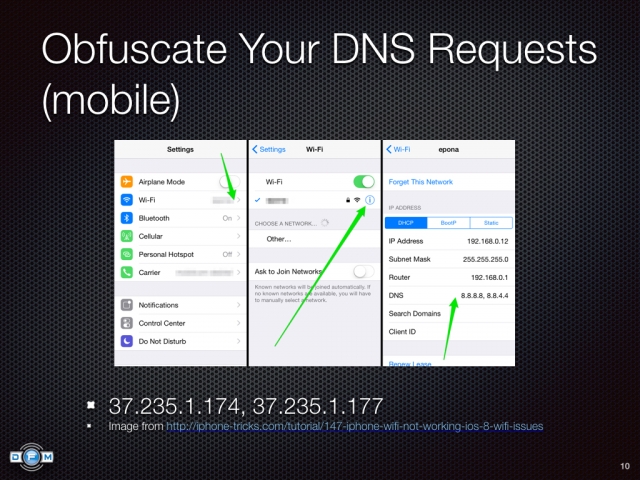 ,
,  ,
,  ,
,  ,
, 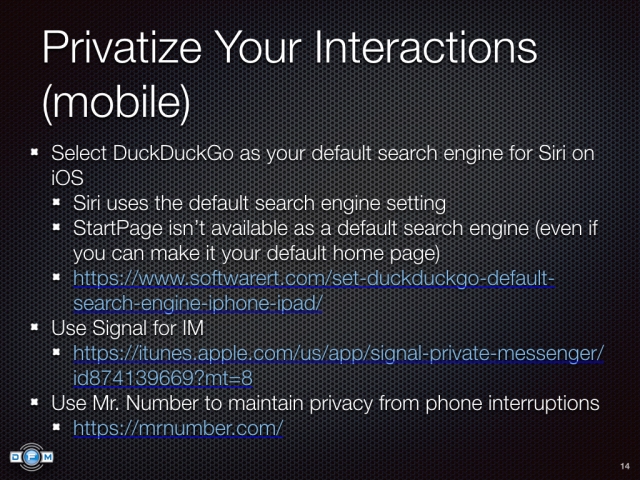 ,
,  ,
,  ,
, 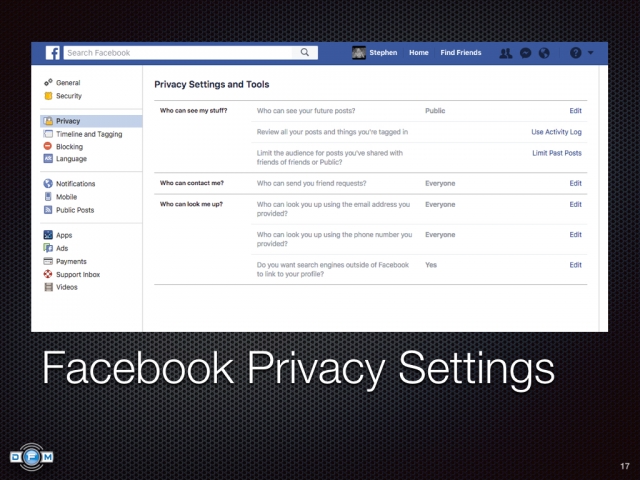 ,
, 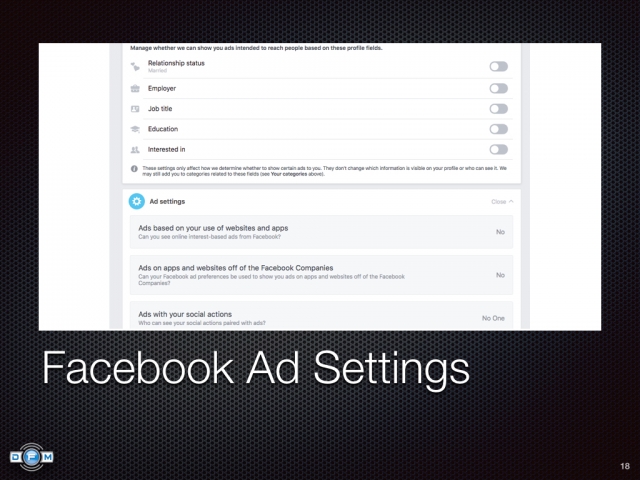 ,
,  ,
, 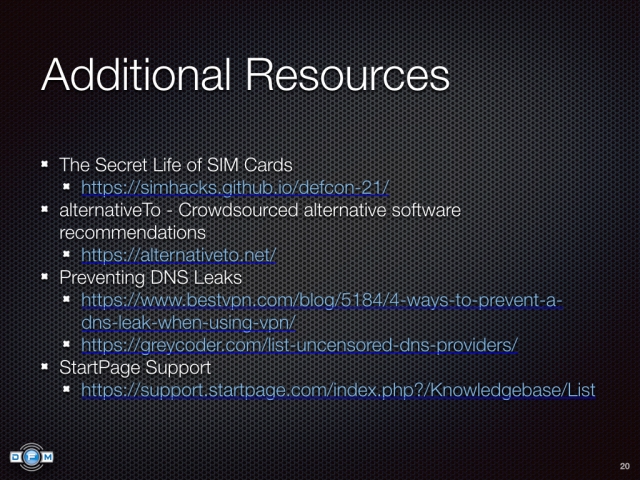 ,
, 
A friend once told me that if everyone is sending envelopes, then sending a package looks suspicious. Earlier today, I spoke at the 2017 DaVinci’s Faire & BarCamp with the goal of getting more people sending metaphorical packages since if everyone sent packages, packages would no longer garner suspicion. Today, it is not completely unheard of for an ISP to send cease and desist notifications to people using TOR--a system that provides privacy and anonymity for online interactions. And many systems out there, including CloudFlare and Atomic Secured Linux, are now purposefully...

Most of those in the development community learned yesterday that their attempts to secure their websites actually left them vulnerable to attack. Beloved CloudFlare typically heralded as a method to shield websites from attack revealed it had a serious bug that leaked memory from "protected" sites that could reveal client IP addresses (one of the big security selling points of CloudFlare), private information, authentication tokens, cookies, passwords, private keys...basically everything that would keep a web developer up at night. CloudFlare stated in a blog post...
